LAB ONE -- COMPUTER NETWORKING
Lab Guidelines:
Lab writeups are generally due one week after completion.
Group lab writeups are encouraged.
The sections to include: introduction and explanation,
OBJECTIVE: The student will become familiar with various automated tools used to probe the Internet. These tools are ping, traceroute, and tracert.
WRITEUP:
Answer these questions from are taken from Chapter 2 in COMER:
- Use ping to test whether you can reach three various computers on the Internet, and list the three round trip times.
- Find one site that is real that you can’t reach, and list its name.
- Ping one site at three times during the day and see if the times vary.
- Experiment with packet size in ping – choose 3 different sizes. Does packet size affect round trip time?
- Compare output from the ping program for a computer that is turned off with the output for a non-existent address [ie. 10.0.0.50]. Do they differ?
- Use the traceroute program to find the number of hops between your computer and remote destinations. What is the maximum number of hops you can find?
- Compare round trip times reported by ping to the number of hops reported by both traceroute and tracert. Is there a correlation between number of hops and a longer delay time?
- Internet technology is documented in a series of reports known as RFC [requests for comments], which are found on the Comer CDROM. Describe two additional tools that the RFC document describes.
- Find one interesting place to telnet to, besides LTU! Some games and libraries have telnet connections. Find one that allows you to login and become a member. Write a small [100 words or less] synopsis on the site, and include its location.
----------------------------------------------------------------------------------
BACKGROUND AND ADDITIONAL INFORMATION
ON Ping, Traceroute, Tracert, and Telnet.
PING……………………………..
To Ping a server via DOS you will need two things
1. Windows 95/98/NT
2. A live connection to the internet
To ping a server click on your MS Window's "Start" button; click on the "Run"
option then type in the word "command" in the pop up window and then select the
OK button. A DOS window will open. Into this window, type "ping useforesite.com"
(note: this DOS environment is case sensitive; make sure all text is lower case.)
Something similar to the following should appear:
----------------------------------------------------------------------------
Pinging useforesite.com [209.239.40.39] with 32 bytes of data:
Request timed out.
Reply from 209.239.40.39: bytes=32 time=245ms TTL=54
Reply from 209.239.40.39: bytes=32 time=244ms TTL=54
Reply from 209.239.40.39: bytes=32 time=218ms TTL=54
Ping statistics for 209.239.40.39:
Packets: Sent = 4, Received = 3, Lost = 1 (25% loss),
Approximate round trip times in milli-seconds:
Minimum = 218ms, Maximum = 245ms, Average = 176ms
--------------------------------------------------------------------------------
Let's break it down:
First line:
--------------------------------------------------------------------------------
Pinging useforesite.com [209.239.40.39] with 32 bytes of data:
--------------------------------------------------------------------------------
useforesite.com is the URL (Universal Resource Locator) which identifies this web site.
It's the same as http://www.useforesite.com. [209.239.40.39] is the IP address. this
number is the numeric address to http://www.useforesie.com
In fact http://209.239.40.39
entered in to your browser will take you to the same place. The URL is a system which is
used to make web surfing easier for humans since we can remember names better than we can
numbers. When a URL like http://useforesite.com is typed into your browser the computer
converts that address to http://209.239.40.39 and sends this number to routers on the
internet. The router's use this number to find ForeSite Design's server so it can display
this page on your browser. To the routers, this page's exact address is
http://209.239.40.30/tut_ping.shtml (tut_ping.shtml is the file name of this page).
The packet size of the file being sent to perform the ping is 32 bytes.
Second line
-----------------------------------------------------------------------------
Request timed out.
--------------------------------------------------------------------------------
This was forced to happen by lowering the available time for the packet to make its trip. Sometimes the internet get bogged down and runs very slowly. This is the error message you will see if it takes too long for the packets to return. The exact default time is approximately on the order of 550 to 750 ms. If you get this error message you can make it go away by increasing the amount of time for the packet to make its trip. This is accomplished by invoking a switch within the ping command.
To see a list of available ping switch options, do the following;
in the DOS window type "ping" and hit the enter key.
The syntax for increasing the time out default time is "ping -w ### useforesite.com" where ### is the amount of time in milliseconds you wish to allow for the packet's round trip. I forced the "Request timed out" by typing in the following:
"ping -w 50 useforesite.com.
If your pings are not returning to you, try increasing this number to 750 or higher if necessary. Ping speeds will often average 150 - 375 ms depending on your type of connection. If you're seeing times in excess of 800 ms, something is probably amiss with the connection. If this is the case, using tracert will help isolate the offending nod.
Lines 3 - 5
--------------------------------------------------------------------------------
Reply from 209.239.40.39: bytes=32 time=245ms TTL=54
Reply from 209.239.40.39: bytes=32 time=244ms TTL=54
Reply from 209.239.40.39: bytes=32 time=218ms TTL=54
--------------------------------------------------------------------------------
Bytes is an indication of the packet size. Time is how long the round trip took in milliseconds and TTL is Time To Live. TTL is a number between 0 and 254 which is assigned to the packet. Each nod, server or router along the way reduces this number by one. If the packet number gets to zero before it reaches it's destination it is discarded. This prevents lost packets from roaming the internet indefinitely.
If you are connected to the internet via a 14,400 modem then the, amount of time for the round trip will be higher than those displayed above. The ISP's modem's speeds in this example are 28,800. If you would like to log directly into LTU’s server and run ping from there then click here. The difference in speeds are significant and this will give you a good idea of how fast information can be sent from one side of the US continent to the other and back. The average time is 30 to 40 ms. That's a factor of seven greater than the above examples and gives you a good idea of where internet bottlenecks are and why some pages are loading slowly onto you browser.
TRACEROUTE TUTORIAL
Diagnosing Slow Connections
All communication across a network is
broken into packets before sending and is reassembled at the receiving end.
Let's say we are sending a 100 page
letter to someone and his mailslot is only big enough for one page at a time.
So we have to send each page in its own envelope with its own addressing and
stamp. Several things can happen:
1.
All the envelopes are delivered without mishap (giggle).
2.
None of the envelopes are delivered (either you or the
receiver
or both are not online or your ISP has router difficulty or Atlanta
has been hit in a pre-emptive tactical nuclear strike).
3.
Some of the envelopes are delivered.
If it is the last case, and it usually
is, success depends on how many of the envelopes are delivered. Some protocols
will try to resend lost envelopes but in the end, there will usually be some
missing information. If you try to read a book with a few missing pages, you
still get the gist of the story as long as the missing pages are not
consecutive and don't include critical plot changes. In the same way, the web
server, ftp server or your local computer can recover from some missing packets
to finish your upload or download.
If say, 95% of the packets arrive
intact, the receiving computer can assume the missing material from context.
For example:
She _ells seashe_l_ by the _eashor_.
Is easily translated into:
She sells seashells by the seashore.
If say, only 80% of the packets arrive
safely, there is not enough to put the whole message back together, this:
_he ___ls __ashe___ b_ the __asho__
is not enough to work with.
If the receiver sees that it has
received less than 80% of say, the first 20% of the message:
__e se___ s_a___
it gives up early and sends a message
like "blocking call canceled" or "connection failed".
Web browsers will give slightly
different error messages.
Missing
or delayed packets will be the cause of 90% percent of your connection
difficulty.
The first step in diagnosing
connection problems is to run a traceroute. This will help to determine what
path your connection takes across the Internet to reach our servers. The
traceroute tool is not intended to gauge your Internet connection as a whole
but to show the specific path you take to a specific location. If you have a
Windows95 or WindowsNT computer, you can use the built-in traceroute program to
do this.
Macintosh users can get a free traceroute utility from allmacintosh.com
Click on the 'start' button and go to 'programs'. Choose 'MS-DOS prompt'
('Command Prompt' in NT) and at the 'c:\windows>' prompt, type:
tracert yourdomainname.com
You will be presented with a string of
numbers representing the connect times of three packets sent to the next server
in line through which you must pass on your way to our server. That
server then sends three packets to the next server in line and reports those
times back to you. If you see an asterisk in place of a connect time, this
means that packet was placed on a network wire at the same time another server
placed a packet on the wire and they overwrote each other (commonly called a
data collision). This is indicative of heavy traffic on that network and three
asterisks on the same line mean that may be a dead connection. In this case we
suggest logging off and logging back on to your ISP to see if you can get a
different connect route. If you see long connect times (consistently in excess
of 400ms), the server on that "hop" may be busy servicing other
packets . This traceroute is only a snapshot of network traffic at that moment
in time. It should be run several times to determine the "trends" of
the traffic. To save it to a file for future reference, type:
tracert yourdomainname.com >
C:\trace.txt
This will create a file in the root
directory of your hard drive named 'trace.txt' that you can then view with
'notepad'. Any subsequent traces can be appended to the trace.txt file with:
tracert yourdomainname.com >> C:\trace.txt
The next step is to determine the path that the server's packets take to you.
You can connect to your site via the built-in Windows95 telnet program. Our telnet
tutorial explains the steps (WindowsNT has the same Telnet program
built-in).
Once you are at the telnet prompt on the server, type:
traceroute 64.20.82.177
The number above should be the IP address of your current connection to the
InterNet. If no number appears, our server was unable to determine your
addresss and you will need to contact your ISP or network administrator.
The results of these server side traceroutes can be cut and pasted into a local
file via notepad.exe or this command will send the results to you via email:
traceroute 64.20.82.177 | mail you@yourdomain.com
The symbol between the the IP address
and "mail" above is known as "the pipe" and should be above
the backslash on your keyboard.
If looking at the results of these
traceroutes, both to and from the server does not yield any obvious answers
regarding your connection, email them to us and we will investigate further. If
the results point to specific traffic congestion somewhere between you and the
sever, logging off your Internet connection and reconnecting may help. This may
cause your ISP to assign you a different temporary local IP address which may
take a different path to our server.
Shopping for ISP's should be done
using the traceroute tool. Many ISP's offer free evaluation periods during
which you may monitor the connection reliability with this tool. Remember to
run the trace several times to get a feel for the "trend" of the
traffic.
TRACERT TUTORIAL
Tutorial - using DOS to-
Trace a route from one PC to another
To run a trace right now you need two
things.
1. You
need to be running Windows 95, 98 or NT
2. You
need to be logged onto the internet.
If you don't have Windows 95, 98 or NT
and consequently cannot perform the functions below then go to a page that provides a program which
will allow you to run traceroute from your serverClick on Window's
"Start" button, then click on the "Run" option. Type
the word "command" in the popup window, don't use the quotations,
then click the OK button. A DOS window will open.
Tracert Options
In this DOS window, type the word
"tracert" and hit the enter key. A menu of switch options will appear
and look like this.
Usage: tracert [-d] [-h maximum_hops]
[-j host-list] [-w timeout] target_name
Options:
-d Do not resolve addresses to hostnames.
-h maximum_hops Maximum number of hops to search for target.
-j host-list Loose source route along host-list.
-w timeout Wait timeout milliseconds for each reply.
If you wish to invoke any of these
options, the syntax is tracert -d hostname.com or tracert -h 12 hostname.com
The default settings work fine and usually
don't need to be changed. The following method invokes a trace without altering
the default settings.
Trace to a host
In the DOS window, type the word
"tracert ####" where
#### is the IP address or URL of the host you want to trace (use lower
case letters). To run a trace to our web site's server (Computer) from your PC, type
"tracert useforesite.com" or "tracert 209.239.40.39" ignore
the quotes. If there are no traffic jams or problems on any of the
routers along the way, you'll see something similar to the following.
*Note: To close this DOS shell
popup window, type the word "exit" and hit enter.
Tracing route to useforesite.com
[209.239.40.39]
over a maximum of 30 hops:
1 196 ms 161 ms 163 ms wg.dvol.com [206.20.144.10]
2 181 ms 160 ms 162 ms irx.dvol.com [206.20.144.1]
3 193 ms 181 ms 204 ms cust-2-frm-4-3.ph.idt.net [169.132.128.113]
4 180 ms 187 ms 188 ms ph-t1.gw-1.dc.idt.net [206.20.128.33]
5 197 ms 161 ms 162 ms core-1-eth-2-3.dc.idt.net [169.132.128.65]
6 216 ms 223 ms 212 ms fddi2-1-0.br1.dca.globalcenter.net [192.41.177.118]
7 189 ms 161 ms 168 ms pos6-0-0-155M.cr1.IAD.globalcenter.net [204.152.166.6]
8 209 ms 175 ms 222 ms fe0-0.cr2.IAD.globalcenter.net [204.152.166.132]
9 224 ms 186 ms 194 ms s3-0.cr1.BWI.globalcenter.net [209.143.255.6]
10 230 ms 216 ms 213 ms alabanza-to-fgc.globalcenter.net [209.143.255.26]
11 250 ms 195 ms 202 ms alabanza-to-fgc.globalcenter.net [209.143.255.26]
12 219 ms 211 ms 215 ms useforesite.com [209.239.40.39]
Trace complete.
This is the route the trace took to
get from the local PC to the address on useforesite's server.
Dissect the information
line by line
Tracing route to useforesite.com
[209.239.40.39] over a maximum of 30
hops:
First line of text
The first line refers to the
useforesite.com URL (Universal Resource Locator) and the respective IP address
[209.239.40.39]. These two identifiers are one and the same. It's easier for
humans to remember words than it is for them to remember numbers so URL's are
used by humans to locate other human's servers while the numbers are used by
computers to locate another computer. URL's were created as a matter of
convenience for people. IP's were the original method for calling another
computer.
Second line of text
= maximum of 30 hops
No! This isn't referring to how many
of your favorite beverages you may consume before getting flagged at your local
bar.
Think of hops, nodes, computers,
servers and PCs as all being pretty much the same thing. This line is saying
"If it takes more than 30 hops to get from this originating PC to the
destination PC's address then stop trying". This number (30) is
configurable by using the -h switch listed above (the syntax is, tracert -h #
hostname.com [where # is the maximum number of hops
for the trace to take]). You may wish to lower this number
but if a trace takes more than thirty hops to anyplace in the world, there's
something seriously wrong.
Lines 1 & 2
1 196 ms 161 ms 163 ms wg.dvol.com
[206.20.144.10]
2 181 ms 160 ms 162 ms irx.dvol.com [206.20.144.1]
Delaware Valley Online
The first three sets of numbers
followed by "ms" is the amount of time in milliseconds that it took
for a packet of information to get from the PC which initiated the trace to the
receiving computer and sent back to the originator on three separate journeys.
The average round trip to the first server was 173ms or (196+161+163) ÷
3 = 173. These times are not cumulative as you pass down the list each
represents the time it took for that individual server to send the packet back.
An easy way to identify the hosting
companies and back bone providers along a traced route is to enter there IP
address into your browsers address pane. Using the above example you could
enter either http://206.20.144.10 or http://www.dvol.com both are the same thing.
What else does line 1 and 2 tell us?
Both are from dvol.com so both are nodes which are probably located at the same
physical facility. They are simply two computers at a single ISP's (Internet Service Provider) facility. Line one
is the first computer that encountered the packets from the trace. Line two is
the second and so on. So the trace first entered the dvol.com facility via the
computer at line # 1 and was routed over to the computer at line # 2 by which
it left the facility and went on to idt.net.
Lines 3 - 5
3 193 ms 181 ms 204 ms
cust-2-frm-4-3.ph.idt.net [169.132.128.113]
4 180 ms 187 ms 188 ms ph-t1.gw-1.dc.idt.net [206.20.128.33]
5 197 ms 161 ms 162 ms core-1-eth-2-3.dc.idt.net [169.132.128.65]
The trace entered idt.net on the
computer at line # 3. This computer has a designation of ph.idt.net.
Again you could visit their web site by pointing your browser to http://www.idt.net . The ph is an interesting
feature as it is an indication of Philadelphia, PA USA.
IDT

The packet at line # 4 (ph-t1.gw-1.dc.idt.net
[206.20.128.33]) has now traveled to a server at idt.net which handles the
Washington DC area (dc.idt.net). This server is located in the Philadelphia
area but routes all packets to the DC area which need to go to DC. This is
shown by the use of ph-tl at the beginning of the address. This server is in
Philadelphia but handles traffic to the DC area.
Line # 5 (core-1-eth-2-3.dc.idt.net
[169.132.128.65]) is indicating that we are still at idt.net but are now on
a server or router at a core or backbone facility in DC. Which is an eth-ernet.
This is an indication of peering onto a major backbone provider of the internet
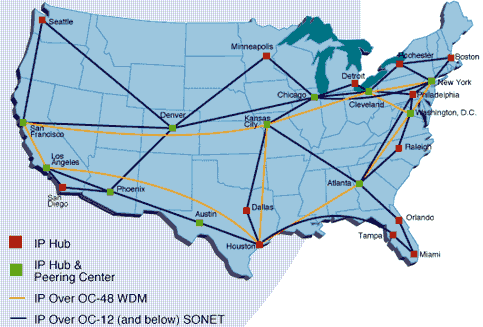
which happens to be MAE East (MAE = Metropolitan Area Ethernet). Note the map
above, courtesy IDT.
Lines 6 - 11
6 216 ms 223 ms 212 ms
fddi2-1-0.br1.dca.globalcenter.net [192.41.177.118]
7 189 ms 161 ms 168 ms pos6-0-0-155M.cr1.IAD.globalcenter.net [204.152.166.6]
8 209 ms 175 ms 222 ms fe0-0.cr2.IAD.globalcenter.net [204.152.166.132]
9 224 ms 186 ms 194 ms s3-0.cr1.BWI.globalcenter.net [209.143.255.6]
10 230 ms 216 ms 213 ms alabanza-to-fgc.globalcenter.net [209.143.255.26]
11 250 ms 195 ms 202 ms alabanza-to-fgc.globalcenter.net [209.143.255.26]
------------------------------------------------------------------------
Lines 6 - 11 are all computers/routers
owned by Global Center. Their address's are not as easily deciphered but there
is some other relevant information worthy of comment. Line # 6 has a 155M
designation in it. This is most likely a reference to a 155 Mbps OC-3 or
Optical Carrier line. This is a fiber optic cable capable of transmission
speeds of 155 Megabytes per second. Very Very Fast.
Global Center
Line 12
12 219 ms 211 ms 215 ms
useforesite.com [209.239.40.39]
Here we are at the destination server (computer). It only took, on average, 215ms or
slightly less than a quarter of a second for a packet of information to be sent
out from a PC in the Philadelphia area through 11 computers over 3000 miles and
back again. That's 22 connections and 6000 miles in a quarter of a second.
Whew! That's fast. Consider this: 80% of that travel time was spent between the
originating PC and the first computers which happens to be an ISP whose modem
connection speeds are limited to 28,800 kbps. That means the trip through 20
servers and 6000 miles really only took 42ms which is only 4 hundredths of a
second.
Other indicators to
look for in a hop:
ATM
can support data transfer rates from 25 Mbps to 622 Mbps,
HSSI transfers up to 52 Mbps comparable to a T3 line at 44
Mbps,
OC3 transfers up to 155 Mbps,
DS3 transfers up to 45 Mbps
Study the following
trace hops to see what you can determine from them.
170 ms 181 ms 156 ms
mae-east.iconnet.net [192.41.177.75]
190 ms 156 ms 168 ms Hssi0-0.balt01.IConNet.NET [204.245.69.49]
174 ms 229 ms 185 ms Serial10-1-0.phi02.IConNet.NET [204.245.69.69]
338 ms 326 ms 304 ms unknown-atm5-0-0.Seattle.cw.net [166.49.26.6]
189 ms 251 ms 198 ms core10-hssi-1.SanFrancisco.cw.net [204.70.10.221]
Tracert is the command that we used in
the DOS window throughout the preceding tutorial. The UNIX equivalent is
traceroute. If you can telnet into your web sites server, simply type in
traceroute hostname.com where hostname is the URL to whatever site you want to
trace or you could type in the IP address like this; traceroute
123.45.678.912.
Locate a host --
Why not just run a trace and use the first backbone provider which has
hosting packages? Backbone providers are big with big overhead. Their time is
money and if you need a personal touch with the web design process expect to
pay a premium price.
To cut down on cost some companies
have dedicated servers at the backbone providers facilities which are coupled
to their access lines. This allows us to have very low overhead and provide a
personal touch without the expense. This should give you a good idea of what
you should expect from a host.
All Things Said And Done
All the above mentioned factors effect
the internet as a whole and it's possible for one to have the best hardware
configuration out there and the site can and probably will suffer from time to
time because of the web surfers path or connection to the site, after all, the
web surfer has to connect through an ISP which connects to a NAP or MAE which
goes through another or multiple NAP's or MAE's which connects to the final
host. Any one of these connections could be a potential bottleneck. Taking care of all the configuration details
on your end will, however, improve your odds for a good connection.
A Telnet
Tutorial -- What is Telnet, Anyway?
The
term "TELNET" refers to the remote login that's possible on the
Internet because of the TELNET Protocol. Telnet allows you to remotely access a
computer over the Internet. In other words, you can tell that computer to
create, edit, execute and delete files just as if you were sitting at that
computer.
The use of this term as a verb, as in "Telnet to a host" means to establish a connection across the Internet from one host to another. Usually, you must have an account on the remote host to be able to login to it once you've made a connection. However, some hosts provide public services that do not require a personal account.
Telnet Fundamentals (Terminal Emulation)
A
long time ago, computers were behemoths that occupied entire rooms. In order
for more than one person to use the computer, "terminals" were
connected to the computer. At first these terminals were teletypes - just fancy
typewriters called TTYs. The computers could tell these TTYs to print
characters, do line feeds and carriage returns, and read input from the person
typing at them. Then CRT (video) terminals were introduced, and ways of
handling characters displayed on a screen had to be developed. These early
terminals included the DEC family of VTs (Video Terminals) like the VT-52 and
the VT-100. They were pretty fancy. They allowed users to do "full screen
editing" by moving a cursor around the screen and deleting characters at
will. They also allowed the computers to print special characters like lines
and dashes, display bold text, or clear the screen entirely.
Nowadays we don't live in caves and hunt mammoth, but we still use this emulation for remote login sessions like Telnet. The emulation of old terminal types, like TTY or VT-100, are good ways of controlling a computer through another computer because they were character based and were designed to transmit and receive data quickly and efficiently.
Connecting to Sites with Telnet
UNIX Commands
UNIX Sites
Basic UNIX Commands
List Contents of Directories - and
[options]
|
ls |
lists
files in current directory |
|
ls
-l |
provides
long listing of current directory |
|
ls
-l /usr/jane |
provides
long listing of directory /usr/jane |
|
ls
-a |
list
all entries (including ones starting with a decimal) |
|
ls
-i |
print
inode numbers |
|
ls
-t |
sort
by modification time |
|
ls
-x |
multi-column
list, sorted across each row |
What would you like to do?
|
ACTION |
Command |
Examples |
|
append
to file |
cat
>> |
cat
>> file |
|
changing
permission group |
chgrp |
chgrp
GroupName FileOrDirectory |
|
combine
2 files |
cat |
cat
File1 File2 > File3 |
|
copy
files |
cp |
cp
MyFile CopyOfMyFile |
|
create
a file |
cat |
cat
> NewFile |
|
edit
files |
ed |
ed
File |
|
list
files |
ls |
ls
usr/mac |
|
move
a file (to directory) |
mv |
mv
MyFile docs/html/mine |
|
remove
a file |
rm |
rm
UnWantedFile |
|
rename
a file |
mv |
mv
OldFilename NewFilename |
|
view
files |
cat |
cat
plan.dec |
|
view
files |
page or more |
page
plan.dec |
|
Change
Login Password |
passwd |
passwd |
|
change
to another directory |
cd |
cd
/usr/tmp |
|
create
a directory |
mkdir |
mkdir
/usr/paul/budget |
|
find
out where you are |
pwd |
pwd |
|
go
to your home directory |
cd |
cd |
|
remove
an empty directory |
rmdir |
rmdir
junk |
Redirection of Output or Input
> redirects the output of a command to a
file
>> redirects the
output of a command to the end of an existing file
< takes the
input of a command from a file, not the terminal
chmod --- Change Access Modes
chmod [mode] files
modes can be numeric or symbolic
The symbolic case consists of the form of [agou][+-=][rwx] where:
|
a |
group,
other and user access permissions(all) |
|
g |
group
access permissions |
|
o |
other
access permissions |
|
u |
user
access permissions |
|
r |
read
permission |
|
w |
write
permission |
|
x |
execute
permission |
|
Example: |
add
write permission for user and group to a file: chmod ug+w files |
|
For
numeric case consult above sites for more details. |
|
|
X-- |
owner's
permission |
|
-X- |
group's
permission |
|
--X |
other's
permission |
where X is the octal sum of 04 (read),
02 (write), 01 (execute) for user, group and other.
Numeric Example: chmod 640 FileOrFolderName
changes permissions so user has read, write permission (4+2+0=6), group has
read permission(4+0+0), and other has no permissions. This makes 640.
--------------------------------------------------------------------------------------------
You
can run Windows Telnet by following the steps below:
- Go to the Start
menu and select Run.
- In the Open:
box, type telnet followed by your domain name (including the .com
or other extension).
- Click OK.
Once a successful connection is established, the login prompt appears as
shown below:

- At the login
prompt, type your username and press Enter.
- At the password
prompt, type your administrative password and press Enter.
For security reasons, your password
does not display on the screen.
After you log in, the welcome screen
appears.
The line at the bottom of the screen
contains your username. This line, with the % symbol at the end, is called a command
prompt. It lets you know that your server is waiting for you to tell it what to
do.
If you’ve made it
this far, congratulations! You’ve successfully established a Telnet session
with your NT Virtual Server`s mail server.
At this point, you
have the following options:
- If you were
referred here from a section within the NT User’s Guide, you can go to the
next step of the particular procedure that brought you here.
- If you want to
learn about your NT Virtual Server’s file system, or want to understand
what the basic Unix commands found in the NT User’s Guide actually do, we
encourage you to go on to Part 2 of this tutorial, The NT Virtual
Server`s mail server File System.
Even if you don’t
care right now why you need to type a particular line at the command prompt,
you can always go back later to learn more about the inner workings of your NT
Virtual Server`s mail server.